Pass-Guaranteed Demo
Download

RedHat Enterprise linux Tutorials Lessons Certification Exams Questions RHCSA RHCE VCP VMWAARE DATA CENTER DESIGN DCD VCAP-DCA Books CBT Virtualization Cloud Software Defined Data Center
Known also as the RedHat Red Hat Certified Engineer on Redhat Enterprise Linux 5 (Labs) (RH302), this exam plays an integral role in obtaining your certification. All RedHat certification exams are extremely detailed and cover many different technological areas. We designed the RH302 questions and answers for this very purpose, to prepare you for the unexpected. Beyond the testing center, the skills you learn and the knowledge you confirm using the RH302 practice exams and exam simulators will translate directly into your daily work environment.
When available, take advantage of the TestKing RH302 Value Pack and save time and money while developing your skills to pass your 'Red Hat Certified Engineer on Redhat Enterprise Linux 5 (Labs) Exam' and grab that RedHat certification. Let us help you climb that ladder of success and pass your RH302 now!

Before You Take your RHCE RHCT Exam:
If you pass all these pre-assessment then you can directly go for RHCE exam, if you are doing good only for RH033 and RH133 then you should go for RHCT or need more preparation.
RH033 exam for RHCT
RH133 exam for RHCT
RH253 exam for RHCE

Linux Timesaving Technique For Dummies provides experienced and first-time Linux users with concise, step-by-step, timesaving,powerful techniques to help them perform tasks efficiently. The techniques, broken down into task-oriented topic areas, are delivered without technical jargon and in the For Dummies friendly, easy-to-understand style. The book corresponds with the latest releases of the Fedora Core, SUSE, and Mandrake distributions. This book is organized into parts groups of techniques about a common subject that will save you time and help you get your system running better. Each technique is written to be independent of the others, so you only need to implement those techniques that are important to you and your users. From time to time, we may send you to another technique to implement a feature that we’ll be using in our current technique we just don’t want to waste valuable space repeating ourselves. Each of the partsis about a different facet of a Linux system so you can scan the part title easily, looking for problemsolving techniques that will help you, quick. It has over 60 techniques that help users perform end-user, system administration, and development tasks in many areas, including the following:
Desktop File system, RPM, Databases, Internet Server, Email Server, Networking, System monitoring, Security, Data Back-up and recovery, Programming (e.g., C and PHP), and Linux Kernel.
Over 60 techniques that help you save time by…
* Controlling time-consuming tasks
* Improving your system security
* Getting the most from your file system
* Automating repetitive tasks
* Tweaking the kernel on your Linux system
* Networking like a professional
The Dummies Way
* Tricks and tips for working smarter
* Explanations in plain English
* "Get in, get out" information
* Contents arranged by technique
* Advice that goes beyond the basics
* A dash of humor and fun
Download
http://rapidshare.com/files/293195431/Linux-Timesaving-Techniques.rar

Red Hat Linux Security and Optimization is a reference for power-users and administrators covering all security issues, including Filesystems Security, Securing root accounts and Firewalls. Application performance benchmarking will also be covered. This book introduces you to many application-specific performance and benchmarking techniques and shows you how to tune your computer as well as your networks. This book covers all the primary Red Hat Linux Applications such as Apache Web Server, WuFTP, FTP server, BIND DNS server, Sendmail SMTP server and focuses on how to enhance security for each of them. It also shows you how to secure NFS and Samba Server, as well as the Apache Web Server.
Contents :-
Part I System Performance
Chapter 1 Performance Basics
Chapter 2 Kernel Tuning
Chapter 3 Filesystem Tuning
Part II Network and Service Performance
Chapter 4 Network Performance
Chapter 5 Web Server Performance
Chapter 6 E-Mail Server Performance
Chapter 7 NFS and Samba Server Performance
Part III System Security
Chapter 8 Kernel Security
Chapter 9 Securing Files and Filesystems
Chapter 10 PAM
Chapter 11 OpenSSL
Chapter 12 Shadow Passwords and OpenSSH
Chapter 13 Secure Remote Passwords
Chapter 14 xinetd
Part IV Network Service Security
Chapter 15 Web Server Security
Chapter 16 DNS Server Security
Chapter 17 E-Mail Server Security
Chapter 18 FTP Server Security
Chapter 19 Samba and NFS Server Security
Part V Firewalls
Chapter 20 Firewalls, VPNs, and SSL Tunnels
Chapter 21 Firewall Security Tools
Appendix A IP Network Address Classification
Appendix B Common Linux Commands
Appendix C Internet Resources
Appendix D Dealing with Compromised Systems
Appendix E What’s On the CD-ROM
Index
http://rapidshare.com/files/273750398/RedHatPress-RedHatLinuxSecurityandOptimization.rar

RHEL 5 Administration Unleashed
Red Hat Enterprise Linux 5 Administration Unleashed blends step-by-step instructions with just enough conceptual knowledge to help RHEL 5 administrators on a daily basis. Why another Linux book you might ask? I have been writing about Linux for years and reading Linux books for longer. When I first started learning Linux, I was frustrated with the lack of detail in most books. I would look up a topic, read all the theory and conceptual sections, and then turn the page expecting to see the actual instructions for implementing what I had read about.
Topics covered include:
* Installing on a single system or on multiple systems simultaneously with Kickstart
* Installing, updating, and removing software with YUM and Red Hat Network
* Navigating the Filesystem from the command line
* Managing storage with partitions, LVM, and RAID
* Using access control lists and disk quotas
* Managing users and groups efficiently
* Performing backups and rapid recovery
* Automating tasks with scripts and scheduling them with cron
* Setting up unified identity management services
* Administering network services for file sharing, network connectivity, an secure
remote login
* Monitoring and tuning system resources, the kernel, and applications
* Protecting against security vulnerabilities with SELinux and ExecShield
* Setting up a firewall with IPTables
* Customing the Linux Auditing System
* Running multiple operating systems concurrently with Virtualization
Contents:-
Introduction
Part I: Installation and Configuration
Installing Red Hat Enterprise Linux
Post-Installation Configuration
Operating System Updates
Part II: Operating System Core Concepts
Understanding Linux Concepts
Working with RPM Software
Analyzing Hardware
Managing Storage
64-Bit, Multi-Core, and Hyper-Threading Technology Processors
Part III: System Administration
Managing Users and Groups
Techniques for Backup and Recovery
Automating Tasks with Scripts
Part IV: Network Services
Identity Management
Network File Sharing
Granting Network Connectivity with DHCP
Creating a Web Server with the Apache HTTP Server
Hostname Resolution with BIND
Securing Remote Logins with OpenSSH
Setting Up an Email Server with Sendmail
Explaining Other Common Network Services
Part V: Monitoring and Tuning
Monitoring System Resources
Monitoring and Tuning the Kernel
Monitoring and Tuning Application
Part VI: Security
Protecting Against Intruders with Security-Enhanced Linux
Configuring a Firewall
Linux Auditing System
Appendixes
A Installing Proprietary Kernel Modules
B Creating Virtual Machines
C Preventing Security Breaches with ExecShield
D Troubleshooting
Download
http://rapidshare.com/files/268714667/RHEL_5_Administration.rar

Visual CertExam Suite is a desktop test engine designed specifically for certification exam preparation. It allows you to create, edit and take practice tests in the environment very similar to a real exam. Visual CertExam Suite includes two applications:
Visual CertExam Designer allows you to create and edit your own professional practice exams.Visual CertExam Manager is designed for taking exams created with Visual CertExam Designer.
Features:-
The most realistic certification exam simulation.
You can work with most of the question types used in certification exams (Multiple Choice, Fill in the Blank, Select and Place, Point and Shoot, Hot Area, Create a Tree, Build List and Reorder, Drop and Connect).
Ability to create case study based exams.
The question preview feature allows the author see exactly how a question will appear during an examination.
Supports question text formatting, including bullets, numbering and alignment.
All exam data (including images) is stored in a single file that simplifies copying and distribution of created exams.
Printing and print preview of exam files.
Supports the most popular image formats: GIF and JPEG.
The Import Wizard lets automatically create exam files from existing text files or RTF-documents with questions.
Ability to work in a local network using file sharing.
You can group questions into sections based on exam topics.
Each exam file can contain multiple instances of an exam (Exam A, Exam B, Exam C and so on).
You can set a password for opening an exam file in Visual CertExam Designer to prevent unauthorized copying, editing and printing of the exam data.
You can restrict the ability to start an exam by setting a password.
Score history tracking.
Doesn't require the installation of additional software.
EMC Storage Certification Exams included:
EMC.ActualTests.E20-001.v2008-08-25.vce
EMC.ActualTests.E20-040.vce
EMC.ActualTests.E20-040.Technology.Foundations.vce
EMC.Actualtests.E20-040.vce
EMC.ActualTests.E20-050.vce
EMC.ActualTests.E20-050.Technology.Foundations.vce
EMC.Actualtests.E20-050.vce
EMC.ActualTests.E20-050.v15.05.06.vce
EMC.ActualTests.E20-070.vce
EMC.Actualtests.E20-070.vce
EMC.ActualTests.E20-320.vce
EMC.ActualTests.E20-322.vce
EMC.Actualtests.E20-340.vce
EMC.ActualTests.E20-500.vce
EMC.Actualtests.E20-510.vce
EMC.Actualtests.E20-512.vce
EMC.Actualtests.E20-520.vce
EMC.Actualtests.E20-522.vce
EMC.Actualtests.E20-530.vce
EMC.Actualtests.E20-532.vce
EMC.Actualtests.E20-533.vce
EMC.Actualtests.E20-580.vce
EMC.Actualtests.E20-610.vce
EMC.Braindumps.E20-593.vce
EMC.Certkiller.E20-050.vce
EMC.ExamWorx.E20-340.v2.73.vce
EMC.KillTest.E20-322.vce
EMC.Pass4Sure.E20-001.v1.0.vce
EMC.TestInside.E20-012.v2.75.vce
EMC.TestInside.E20-535.v3.28.vce
EMC.TestKing.E22-183.vce
Hitachi Storage Certification Exams included:-
Hitachi.ActualTests.HH0-110.vce
Hitachi.ActualTests.HH0-120.98q.vce
Hitachi.ActualTests.HH0-120.vce
HP Proliant Server Certification Exams included:-
HP0-053 Enterprise Integration and Management of HP ProLiant Servers.vce
HP0-055 Implementing HP ProLiant Servers Brain dumps.vce
HP0-055 Implementing HP ProLiant Servers.vce
HP0-065 Planning and Designing ProLiant Solutions for the Enterprise.vce
HP0-500 HP Proliant Server Maintenance.vce
HP.Actualtests HP0-697 HP ProLiant Systems Technologies Exam.vce
HP.Actualtests HP0-794 Implementing Windows 2003 on HP ProLiant Clusters.vce
HP.ActualTests.by.SSB HP0-794 Implementing Windows 2003 on HP ProLiant Clusters.vce
HP.Actualtests.HP0-645 Implementing HP ProLiant Servers.vce
HP.ActualTests.HP0-725 Implementing Enterprise Integration and Management of HP ProLiant.vce
HP.ExamPrepGuide HP0-725 Implementing Enterprise Integration and Management of HP ProLiant.vce
HP.Pass4Sure.HP0-698 Supporting the HP ProLiant Storage Server Product Family.vce
HP.TestKing HP0-645 Implementing HP ProLiant Servers.vce
HP.TestKing HP0-683 Implementing HP ProLiant Servers.vce
HP.TestKing.HP0-683 Implementing HP ProLiant Servers.vce
HP.TestKing.HP0-697 HP ProLiant Systems Technologies Exam.vce
HP.TestKing.HP0-794 Implementing Windows 2003 on HP ProLiant Clusters.vce
HP.TestKing.v1.0.HP0-725 Implementing Enterprise Integration and Management of HP ProLiant.vce
HP.TestKing.v3.1.214 HP0-725 Implementing Enterprise Integration and Management of HP ProLiant.vce
HP.TestKing.v4.0.HP0-725 Implementing Enterprise Integration and Management of HP ProLiant.vce
HP.TestKing_HP0-697 HP ProLiant Systems Technologies Exam.vce
HP.TestKing_HP0-725 Implementing Enterprise Integration and Management of HP ProLiant.vce
RedHat Linux Certification Exams:-
Red Hat 1.vce
Red Hat 2.vce
Red Hat 3.vce
Note:-
Visual CertExam Suite premium included in the download link with all exams file.
Play all the .vce exam files in the Visual CertExam Suite package exam simulator.
http://rapidshare.com/files/249912210/EMC_HP_Redhat_Hitachi_Exams_VCE.rar

Apache is probably the most popular Linux-based Web server application in use.Web sites both personal and commercial can be very rewarding exercises as they share your interests with the world and allow you to meet new people with whom to develop friendships or transact business.Unfortunately,even the best Web sites can be impersonal as they frequently only provide information that the designer expects the visitor to need. E-mail, although ancient in comparison to newer personalized interactive Internet technologies, such as IP telephony and instant messaging, has the advantage of being able to relay documents and other information without interrupting the addressee. This allows them to schedule a response when they are better prepared to answer, a valuable quality when replies need to be complex.
Video Contents :-
01. Introduction & Course Outline
02. Introduction To Apache
03. Installing Apache on Linux
04. Installing Apache on Windows
05. Configuring Apache on Linux
06. Managing Content on Apache Server
07. Configuring MySQL on Apache
08. Configuring PHP on Apache
09. Apache Web Server Admin
10. Security Testing Apache
11. Securing Apache
12. Best Practices to Running Apache
Download
http://rapidshare.com/files/268997064/VTC_-_INTRODUCTION_TO_APACHE_WEB_SERVER.7z

LinuxCBT RegEx Edition focuses on the application of POSIX and Perl-compatible
Regular Expressions.
Regular Expressions are critical to efficiently parsing textual data (log file
content, data feeds, files & directories, etc.). RegEx support is included with
Linux | Unix operating systems via ubiquitous tools such as: grep, awk, sed, Perl,
PHP, etc., and provides systems administrator/engineers and developers alike, the
ability search, time-effectively, considerable amounts of textual data, using literals,
character classes, metacharacters, metasequences, etc.
Let LinuxCBT RegEx Edition cost-effectively teach you Regular Expressions!
Recommended Prerequisites for:
* Any LinuxCBT Operating System Course (Classic/EL-4/SUSE/Debian Editions)
o Open mind & determination to master Linux and related open-source applications
o Basic understanding of networking concepts
o Access to a Linux system to follow the exercises
See the URL for all the rest of the information.
http://www.linuxcbt.com/products_linuxcbt_regex_edition.php
http://www.filefactory.com/file/c4e7db/
http://www.filefactory.com/file/842c4f/
http://www.filefactory.com/file/1d27da/

LinuxCBT IPv6 Edition focuses exclusively on the burgeoning Internet Protocol Version 6 (IPv6).
The coursework explores IPv6 implementation on today's mainstream Network Operating Systems (NOSs), including: GNU/Linux, Solaris, Windows and Cisco IOS.
Given the imminent depletion of globally-unique 32-bit IPv4 addresses, and mandates set by the US Government with respect to IPv6-backbone-compliancy by Q2 2008 for government agencies, Information Technology (IT) Network/Systems Engineers/Administrators/Integrators/Directors/etc., are tasked with preparing their backbones and applicable infrastructure(VLANs/DMZs/etc.) to support Internet Protocol Version 6 (IPv6).
LinuxCBT IPv6 Edition will prepare you and/or organization to comfortable integrate IPv6 into your production environments, without negatively impacting IPv4 services.
Recommended Prerequisites for:
Any LinuxCBT OS Edition such as LinuxCBT feat. SUSE® 10 Enterprise Edition
Open mind & determination to master Linux and related open-source applications
Basic MS Windows skills
Basic understanding of networking concepts
Access to a PC to perform all of the installations and exercises
http://rapidshare.com/files/44521580/LinuxCBT_IPv6_Edition.nfo.html
http://rapidshare.com/files/44521686/LinuxCBT.IPv6.Edition.sfv.html
http://rapidshare.com/files/44527716/LinuxCBT.IPv6.Edition.rar.html
http://rapidshare.com/files/44548346/LinuxCBT.IPv6.Edition.r00.html
http://rapidshare.com/files/44562437/LinuxCBT.IPv6.Edition.r01.html
http://rapidshare.com/files/44617742/LinuxCBT.IPv6.Edition.r02.html
http://rapidshare.com/files/44706825/LinuxCBT.IPv6.Edition.r03.html
http://rapidshare.com/files/44819836/LinuxCBT.IPv6.Edition.r04.html
http://rapidshare.com/files/44846543/LinuxCBT.IPv6.Edition.r05.html
http://rapidshare.com/files/44902016/LinuxCBT.IPv6.Edition.r06.html
http://rapidshare.com/files/44925386/LinuxCBT.IPv6.Edition.r07.html
http://rapidshare.com/files/44921393/LinuxCBT.IPv6.Edition.r08.html

dd is a perfect tool for copy a file, converting and formatting according to the operands. It can create exact CD-ROM ISO image.
This is useful for making backup as well as for hard drive installations require a working the use of ISO images.
How do I use dd command to create an ISO image?
Put CD into CDROM
Do not mount CD. Verify if cd is mounted or not with mount command:
# mount
If cd was mouted automatically unmout it with umount command:
# umount /dev/cdrom
OR
# umount /mnt/cdrom
Create CD-ROM ISO image with dd command:
# dd if=/dev/cdrom of=/tmp/cdimg1.iso
Where,
* if=/dev/cdrom: Read from /dev/cdrom (raw format)
* of=/tmp/cdimg1.iso: write to FILE cdimg1.iso i.e. create an ISO image
Now you can use cdimg1.iso for hard disk installation or as a backup copy of cd. Please note that dd command is standard UNIX command and you should able to create backup/iso image under any UNIX like operating system.

This information has been compiled to help system administrators certify that good security practices are being used BEFORE a computer is connected to the network.
Installing System Patches
It is recommended that based on the requirement, you install every patch recommended for your computer which isn’t
yet installed. Since some patches restore default configurations, it’s important that patches are put in place before any further security precautions are taken.
Before Recording System Defaults
Before starting to record system defaults, a directory should be created to store them. For example;
mkdir /usr/adm/checksIf an unauthorized user does gain access to root privileges on the computer and changes the accounting system, the
administrator will still have an original copy of it for comparison. For safety, the system administrator should check the files against the original about once a month.
Recording SUID and SGID Programs
Before any software is added to the basic operating system release, the system administrator should check for SUID and SGID programs. If unauthorized access occurs, frequently the intruder will leave a program that enables privileged
re-entry. The list of SUID and SGID programs should be stored both on and off the computer. The version on the computer will be used by a daily cron job to check for changes, while the version stored off of the computer will ensure that even if root access is acquired, a record of the system’s original state is available.
The command to list SUID and SGID files is:
find / -type f \( -perm -002000 -o -perm -004000 \)-type f: looks only at regular files-perm: checks for permissions-002000: checks for SGID programs-004000: checks for SUID programsCheck and Record Permissions on all Device Files
By changing the permissions on device files, an unauthorized user can gain access to devices, using this access to change files, impersonate another user, or listen in on conversations. Record the permissions on the device files on and off the computer using:
ls -al /dev/* sort > /usr/adm/checks/devicesPasswords and Shells on System Accounts
Check the system password file to ensure that all accounts have passwords. Many vendors ship their computers with no passwords on the system accounts. System accounts such as bin, lp, and sync should have a ‘*’ for the password field. No account should be left without a password.
Also, the system administrator should check to see if the computer comes with any passwords already assigned. Some
vendors give default passwords to system accounts. Since anyone who has the same type of system knows what the default passwords are, passwords should be changed immediately.
Every account needs to have a shell assigned to it. Most administrative accounts should have /bin/nologin as the shell, which
would disallow crackers from gaining shell access using obscure system holes.
Expire Inactive Accounts
Computers with large numbers of users tend to have accounts that become inactive. The beginning of a new fiscal year often
brings changes in who is using the computer, as users’ funding sources change. The system administrator needs to be sensitive to those accounts that become inactive, and disable them by replacing the password field in the /etc/password file with an ‘*’. If the user has left important data on the computer, eventually they will contact the system administrator to make arrangements to retrieve the data. Once this data is retrieved, the account should be removed.
Restrict Root Login to the Console
The ability to login to the root account should be restricted to the console. Anyone not at the console should have to use ’su’ to
become root. Tries to ’su’ are recorded in a file in /usr/adm such as /usr/adm/sulog, for accounting purposes
Check for Duplicate Groups
Replace any duplicated group with a group of its own. This will remove ambiguity and make membership in a group clearer.
Do Not Establish Guest Accounts
Do not establish accounts for guest usage. These accounts, often appearing as an account with login guest and password
account, are common holes exploited by unauthorized users. Every user of the computer should undergo the same security procedures, receive the same security briefing, and be held accountable to the same standards. When users are finished using the computer, their accounts should be removed from the password file.
‘remote’ Commands
Commands preceded by the letter ‘r’, such as ‘rlogin‘ or ‘rsh‘, should be disabled. They are a source of many attacks on sites
across the Internet. If you must use ‘r’ commands, make sure you filter the TCP ports (512,513,514) at the router; it is important to note this will only stop outsiders from abusing the commands.
Double Check the System Before Long Weekends
Double check the computer before long weekends to ensure there are no security problems with it. A backup just
before a long weekend is advisable.
Do a Monthly System Check
Run the cron script against the cron stored on the removable media in case the unauthorized user gained root access and altered the system without being noticed.
System Security Diary
Keep a diary of the security checks done on the computer and what their results are. Also, document what actions are taken if holes are found or problems occur. If there is a problem, others will want to know what the system administrator has been doing to secure the computer.

VTC – Unix Shell Fundamentals Tutorials
Author: Mark Virtue
SKU: 33257
ISBN: 1930519915
Release Date: 2001-09-18
Duration: 10 hrs / 90 lessons
Compatibility: Win XP, 2000, 98, NT, Mac OS X, OS 9
Work Files: Yes
UNIX is a family of operating systems. UNIX Shell is common in text-based or command-line UNIX programs. The commands of UNIX shell are compatible with all brands of UNIX, including Linux. This Virtual Training Company tutorial teaches the fundamentals of UNIX Shell even if you have no prior knowledge of UNIX or UNIX Shell commands. Author Mark Virtue helps you get a better understanding thorough demonstrations of processes such as logging in, copying files, combining programs, using telnet, and more. To get started learning from this experienced instructor now, simply click one of the topics below
1. Introduction
About this Course (03:51)
Audience and Prerequisites (03:19)
2. Understanding UNIX
What is UNIX? (07:17)
UNIX History (06:31)
Which UNIX? (07:14)
UNIX Architecture (07:13)
3. Understanding the UNIX Shell
What is the UNIX Shell? (08:59)
Which Shell? (06:59)
Logging In (09:15)
Basic Commands (06:04)
Command Syntax (06:38)
Getting Help (05:11)
Logging Out (02:43)
4. Files and Directories
Working with Files and Directories (07:27)
Commands for Files and Directories Pt 1 (07:54)
Commands for Files and Directories Pt 2 (04:20)
Filenames and File Types (06:48)
Wildcards Pt 1 (05:29)
Wildcards Pt 2 (06:19)
Displaying File Contents (04:00)
Comparing Files (04:44)
Copying, Moving and Renaming Files (07:47)
Deleting Files (05:41)
Hidden Files (06:16)
The “.” and “..” Directories (04:41)
Relative vs Absolute Paths (06:13)
Working with Directories (04:16)
Finding Files (09:37)
Archiving Files (10:29)
5. Security
Users and Groups (07:38)
Security Related Problems (07:18)
File Protection Overview Pt 1 (05:23)
File Protection Overview Pt 2 (04:57)
Changing File Permissions (11:02)
Changing File Ownership (03:26)
Changing File Group (01:27)
A Dangerous Security Loophole (04:34)
6. Combining Programs – Pipes and Filters
Introduction to Combining Programs (00:43)
Standard Output (10:53)
Standard Input (09:16)
Standard Input and Output (05:37)
About Filters (02:20)
Common Filters (08:59)
Searching for Text in Files (08:25)
Standard Error (10:13)
7. Process Control
About Processes Pt 1 (05:10)
About Processes Pt 2 (09:28)
Running Commands Asynchronously (06:37)
Killing Processes (05:55)
Jobs (04:42)
More Process Control (09:08)
Scheduling Commands (06:15)
8. vi – A UNIX Text Editor
Understanding vi (10:01)
Starting vi (04:27)
Manipulating Files in vi Pt 1 (07:35)
Manipulating Files in vi Pt 2 (05:53)
Moving Around Pt 1 (08:07)
Moving Around Pt 2 (07:08)
Basic Editing Pt 1 (08:43)
Basic Editing Pt 2 (05:53)
Basic Editing Pt 3 (06:58)
Advanced Editing Pt 1 (09:05)
Advanced Editing Pt 2 (03:50)
Configuring vi Pt 1 (07:42)
Configuring vi Pt 2 (04:28)
9. The UNIX File System
Introduction to the Unix File System (01:46)
How Files are Stored (10:16)
Understanding Links Pt 1 (06:43)
Understanding Links Pt 2 (07:18)
Linking Files (07:24)
Symbolic Links Pt 1 (06:36)
Symbolic Links Pt 2 (06:00)
UNIX File Types (05:56)
Mounting Pt 1 (06:27)
Mounting Pt 2 (08:12)
10. Communication
Using telnet (08:08)
Using mail (09:28)
11. Customising Your Shell Environment
Changing your Login Shell (05:51)
Environment Variables Pt 1 (07:36)
Environment Variables Pt 2 (06:13)
Your PATH Pt 1 (06:40)
Your PATH Pt 2 (05:31)
Your Prompt (05:33)
Your .profile (07:00)
Command-line Editing (04:41)
Korn Shell Command-line Editing (07:05)
Shell Customisation Options Pt 1 (04:32)
Shell Customisation Options Pt 2 (05:39)
The End (01:46)
download Here
password = tactools.org
http://hotfile.com/dl/255778/48edada/VTC20-20Introduction20to20UNIX20shell.part1.rar.html
http://hotfile.com/dl/255780/47181aa/VTC20-20Introduction20to20UNIX20shell.part2.rar.html
Mirror
http://rapidshare.com/files/221988414/VTC_20-_20Introduction_20to_20UNIX_20shell.part2.rar
http://rapidshare.com/files/221988728/VTC_20-_20Introduction_20to_20UNIX_20shell.part1.rar

Determining File Content
Files can contain many different types of data. The contents of any given file might be ASCII or binary.
ASCII files include, but are not limited to, these types:
Plain text
HTML
Executable shell scripts
C program source code
Mailbox-format text
Binary files include, but are not limited to, these types:
Compiled executables
Compressed data
Images
Sound samples



Nautilus is a graphical filesystem browser provided as part of the GNOME graphical environment. Although managing files from the command line can be more versatile and powerful, many people find a graphical interface to be more intuitive.
Nautilus can run in either of two modes:
Spatial mode
Browser mode
Spatial mode is designed to be the most intuitive for new users and is the simplest in terms of user-interface clutter. Windows have a very basic layout with no toolbar; when a directory is double-clicked it opens in its own window. A menu in the lower-left of each window allows the user to list and select parent directories of the one currently displayed. Typing Ctrl-Shift-W closes all parent windows.
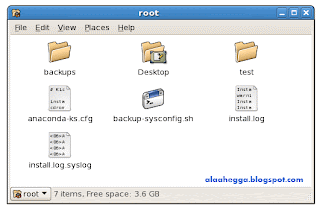
Spatial mode
Browser mode provides a more traditional file-manager interface with a side pane on the left that can display file details, a filesystem tree, or even notes the user has taken about the contents of a directory. The categories displayed in the sidebar can be selected from a drop-down menu. Folders open in the same window instead of in new ones, and the user navigates using the standard back, forward, and up icons available in most graphical file managers.
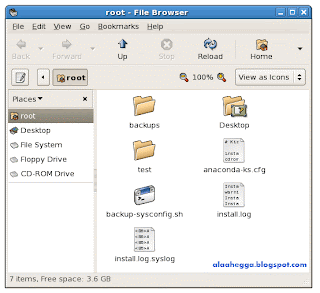
Browser mode
To access Nautilus, use one of the following methods:
Desktop icons
Computer icon
Home directory icon
Removable device icons (CD-ROMs, USB drives, floppy disks)
Menu option
Applications > System Tools > File Browser
The two most common ways to access Nautilus are via desktop icons or a menu option. The desktop icons labeled Computer, and for example, Joe’s Home will each open a Nautilus window in spatial mode. The Home icon opens a window that displays the user’s home directory. The Computer icon opens a window that presents an ordered view of available filesystem resources. This includes the Filesystem icon, which opens a window displaying the root directory; the Network icon, which allows the user to browse the local network for shared disks; and an icon for each removable media filesystem, such as those on CD-ROMs, floppy disks, and USB drives.
Nautilus can be started in browser mode by selecting File Browser from the Applications menu under System Tools in the upper left corner of your GNOME desktop. If you would like Nautilus to always start in browser mode, even when accessed via the desktop icons, open a Nautilus window, select Edit > Preferences from the menus, go to the Behavior tab, select Always open in browser windows and click Close.
Moving and Copying in Nautilus
The following keyboard shortcuts apply to Drag-and-Drop in Nautilus:
Drag
Moves on the same filesystem, or copies if on a different filesystem
Drag + Ctrl
Always copies
Drag + Alt
Asks whether to copy, move, or create a symbolic link (alias)
If the destination is on the same filesystem as the source, when you drag and drop files, Nautilus will move the file instead of copying it. To force Nautilus to copy instead of move, drag the file to its destination and press Ctrl before releasing the mouse button. Holding the Alt key instead will make Nautilus ask whether to copy, move, or create a symlink. A symlink, or symbolic link, is an alias to the source file that does not take up extra space on the drive.
Right-clicking an object in Nautilus opens context menu listing actions you can take on that item. The exact contents of the context menu depend on what is being clicked (the "context" of the click). For files or directories, the context menu includes options to copy, cut (move), or rename the selected object. If you cut or copy a file or directory and then right-click your desktop or a directory, then the context menu will include a paste option. Selecting this option will copy or move (depending on whether the source file was copied or cut from its original location) the previously selected object (or objects) into the directory.

Changing Directories
The shell prompt displays the last component of the directory name, for example, it displays student01 to represent /home/student01. To move from directory to directory on the system, use the cd command.
The cd command accepts one of two arguments:
An absolute or relative path name
A shortcut representing the directory to which you wish to change
A number of shortcuts are at your disposal for use with the cd command. A dot (.) and a double dot (..) are two shortcuts found in every directory. The . shortcut represents the current directory, whereas the .. shortcut represents the parent directory.
For example, if your current working directory is /home/student01, what would typing the following do?
cd ..
It would move you to the /home directory.
The tilde (~) is an abbreviation for “home directory.” Used by itself, it represents your own home directory. Used as a prefix to another user’s login ID, it represents that user’s home directory.
A dash (-) represents your previous working directory. It’s a handy shortcut to use to switch back and forth between two directories.
For example:

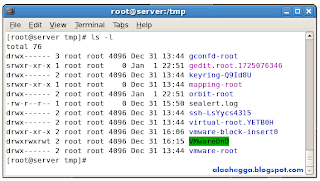
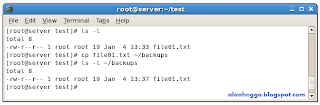
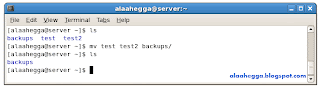

Filesystem Principles
In this lesson, you will study Linux file hierarchy principles. You will learn about the contents of some important directories, some rules for naming files and directories, and how to display the current working directory. You will also look at the difference between absolute and relative path names.
Linux File Hierarchy Principles
Filesystem Basics
These Linux file hierarchy concepts will be expanded upon in the pages that follow:
• A single-rooted, inverted-tree structure is used for organizing files and directories, including distinct physical volumes, such as floppy disks, CD-ROMs, and multiple hard drives.
• The base of the inverted-tree hierarchy is known as root, or /, and is the top of the file structure.
• A forward (/) slash separates elements of a path name, for example /usr/bin/X11/X.
• Names in the Linux file hierarchy are case sensitive.
• Each shell and process on the system has a designated current or working directory.
• Two dots (..) refer to the parent directory of any particular directory, which is one level up in the file hierarchy.
• One dot (.) refers to the current directory.
• Files and directories whose names begin with a dot (.) are hidden, that is, they are not displayed by default in file-name listings.
• A user's path is a list of directories that are searched for commands typed at the command line.
Note:
Linux uses the forward slash (/) to separate elements of a path name, whereas DOS (Windows) uses a back slash (\).
Present Working Directory
The present working directory is the directory in which you are currently working. To view the present working directory, use the pwd command. When you type the pwd command at the command line, the absolute path to your current working directory is displayed. For example
Absolute and Relative Path Names
The location of a directory or file can be specified by either of two arguments: its absolute path name or its relative path name. An absolute path name has these characteristics:
Begins with a forward slash (/)
Contains the complete name of each directory that must be traversed from the root file system up to the object being named
Can be used anytime, and is valid regardless of the current directory
A relative path name has these characteristics:
Does not begin with a forward slash (/)
Specifies the location of the file or directory relative to the current working directory
Is usually shorter than the respective absolute path name

What is Sabily ?
Sabily is an operating system, like MS Windows or Mac OS X. Without an operating system, a computer is unusable, and Windows is not the only OS available! (though you often don't have the choice, that's why we are working hard to fix the bug number one)
I already have Windows, why would I use Sabily ?
Because Sabily is free, already includes all software you need in your everyday tasks, and is customized specifically for Muslims. And even if you didn't buy Windows, you should not use pirated copies because then you are still supporting Microsoft by adding to the impression it's the only OS available.
It should be a tremendous work to develop an operating system?
Actually we don't start from scratch, we use the Ubuntu operating system as a groundwork. Ubuntu is a GNU/Linux distribution whose goal is to provide an easy-to-use, up-to-date, stable and free system, also for companies. Sabily customizes Ubuntu by removing, modifying and adding software, and also customizes the graphic design to make a system adapted to Muslims.
Is there a company like Microsoft which develops Sabily?
No there isn't, just a communauty of voluntaries coming from all over the world (France, Tunisia, Egypt, Indonesia etc.). You can as well participate, as a developer, a graphic designer, a tester or if you just want to share your ideas.
What are the main features of Sabily?
The main software are: Zekr and Mus-haf Othman (Quran study tools), Minbar and Firefox-praytimes (prayer times applications), Monajat (application that popups prayers every predetermined time), Hijra (islamic calendar) and WebStrict (parental control tool). Arabic language is also well supported. And of course the graphic design is also customized (see screenshots).
What other software are included in Sabily?
OpenOffice (word processor, spreasheet, presentation), Firefox (web browser), Pidgin (instant messaging), F-spot (photos management), Gimp (image manipulation program) and other multimedia software (video/audio). All of this in included in the "small" version of Sabily, but the "full" version contains dozens of other software! (educational software, tools and entire Quran recitations, see the full list here)
Sabily seems very interesting, what should I do to use it?
You have to download the ISO file and to burn it on a DVD, then to start your computer from the DVD. You will have the choice to test or to install the system. In a first time we advise you to test it because it is safe for your computer, nothing will be written on your hard disk. You can even test Sabily directly from Windows, by using a Virtual Box image.
