Exercise 01
Backup script for the sysconfig directory
STEP 1
create file using vi editor backup-sysconfig.sh
[root@server ~]#vi backup-sysconfig.sh
step 2
paste the following script
#!/bin/bash
# This script creates a backup of /etc/sysconfig
# into a datestamped subdirectory of ~/backups/
cp -av /etc/sysconfig ~/backups/sysconfig-$(date '+%Y%m%d')
echo "Backup of /etc/sysconfig completed at: $(date)
step 3
copy this file from home directory to the /bin
step 4
create the backup directory on the root home directory
[root@server ~]#mkdir backups
step 5
make this file executable by writing the following command
[root@server ~]#chmod u+x ~/bin/backup-sysconfig.sh
step 6
You are now ready to try out your script. You should see something like the following:
[root@server ~]# backup-sysconfig.sh
`/etc/sysconfig' -> `/root/backups/sysconfig-20100102'
`/etc/sysconfig/pand' -> `/root/backups/sysconfig-20100102/pand'
`/etc/sysconfig/ipmi' -> `/root/backups/sysconfig-20100102/ipmi'
`/etc/sysconfig/rhn' -> `/root/backups/sysconfig-20100102/rhn'
`/etc/sysconfig/rhn/up2date' -> `/root/backups/sysconfig-20100102/rhn/up2date'
`/etc/sysconfig/rhn/clientCaps.d' -> `/root/backups/sysconfig-20100102/rhn/clientCaps.d'
`/etc/sysconfig/rhn/rhnsd' -> `/root/backups/sysconfig-20100102/rhn/rhnsd'
`/etc/sysconfig/kudzu' -> `/root/backups/sysconfig-20100102/kudzu'
`/etc/sysconfig/dund' -> `/root/backups/sysconfig-20100102/dund'
step 7
Now check the backup directory
[root@server ~]# cd backups/
[root@server backups]# ls
sysconfig-20100102
[root@server backups]# cd sysconfig-20100102/
[root@server sysconfig-20100102]# ls
apmd crond ip6tables-config modules sendmail
apm-scripts desktop ipmi network smartmontools
auditd dund iptables networking spamassassin
authconfig firstboot iptables-config network-scripts squid
autofs grub irda ntpd syslog
bluetooth hidd irqbalance pand system-config-securitylevel
cbq httpd kdump prelink system-config-users
clock hwconf kernel readonly-root tux
conman i18n keyboard rhn vncservers
console init kudzu saslauthd wpa_supplicant
cpuspeed ip6tables mkinitrd selinux
Thursday, December 31, 2009
Exercise 01 Bash scripting Practical Examples
Saturday, December 26, 2009
%10 Discount on RHCE exam
%10 Discount on RHCE exam at Alkhobara Training Center in Riyadh KSA
Address (Map) Postal Address
Olaya St. Riyadh Olaya Bldg,
Office #20
Tel: +966 1 229 1917
Fax: +966 1 263 0993 P O Box 101952
Riyadh, 11629
Saudi Arabia
Sales Contact
Toll
Free: 800 122 0001
Fax: +966 1 263 0993
Email: training@alkhobara.net
http://www.alkhobara.net/
Tuesday, December 22, 2009
Lesson05:Finding Help
Don’t try to memorize everything. Instead, learn to use the resources at your disposal. You have many levels of help available:
• The whatis command
• The man command
• The info command
• The --help command option (for command-specific help)
• The /usr/share/doc directory
• Red Hat documentation
The command-line interface has many advantages, but also has a disadvantage. The disadvantage is the sheer number of commands and arguments that the user must take advantage of to use it well. A common mistake by people new to the command-line is to assume they have to commit every little argument to memory.
To be proficient, you don’t need to become a walking database of Linux arcana (though that does tend to come with time). In fact, although committing regularly used commands and arguments to memory is always helpful, the key to effectively using a command-line operating system is the ability to use the available resources to quickly look up arguments and techniques that you do not know by heart. The following slides will discuss several such resources.
The whatis Command
The whatis command has the following functionality:
• Displays short descriptions of commands
• Uses a database that is updated nightly
• Often is not available immediately after install
In day-to-day usage of Red Hat Enterprise Linux, you will periodically encounter a command that looks interesting but whose function is unknown to you. One way to find out what a command does is to run it, but this can be risky. The whatis command provides an easier and safer way of getting a quick explanation of what another command’s function is.
The usage of the whatis command is as follows:
whatis command
For example:
The whatis command accepts the name of another command as its only argument and then searches for the given command name in a database of short descriptions. If it finds a match, the description is printed to your screen. Along with the description, whatis prints the command’s name and a number in parenthesis. This number represents the "chapter" of the Linux Manual where more thorough documentation can be found. Later screens will explain the Linux Manual and the associated man command in more detail.
The --help Option
==========================
In order to use a command effectively, not only do you need to know what a command does, you also need to know what options and arguments the command accepts and what order it expects them in (the syntax of the command).
One good way to determine the syntax or usage of a command is by using the --help command option.
Syntax for the --help option is as follows:
command --help
Most commands have a --help option. The --help option displays a usage summary and a listing of the available arguments. It works with most, but not all, commands.
At first glance, usage statements may seem complicated and difficult to read. However, they become much simpler to understand once you are familiar with a few basic conventions:
• Anything in braces ([]) is optional
• Anything followed by an ellipsis (...) represents an arbitrary-length list of that thing
• Multiple options separated by pipes () means that you can use any one of them
• Text in angle brackets (<>) represents variable data. So
So, look at the first usage statement for the date command:
date [OPTION]... [+FORMAT]
You see that date can take an optional list of options ([OPTION]...) followed by an optional format string prefixed with a plus sign, which defines what you want the date to look like ([+FORMAT]). Since both of these are optional, date will work even if it is not given options or arguments (it will print the current date and time using its default format).
Reading Usage Summaries
Reading Usage Summaries
Usage summaries are printed by the --help, man, and other commands and are used to describe the syntax of a command.
[] Arguments in braces ([]) are optional
<> or CAPS Arguments in angle brackets (<>) or uppercase are variables
…Text followed by an ellipsis (…) represents a list
xyz Means x,y or z
-abc Means any mix of –a , -b , or –c
The man Command
Just about every command, most configuration files, and several developers’ libraries on a Red Hat Enterprise Linux system has an associated man page. The man page provides more thorough documentation than the --help option does.
To access the man page for a command, use the following syntax:
man [section/chapter] command
For example:
man ls
Manual pages normally contain sections discussing aspects of a command’s usage.
These sections include:
• The NAME of the command and a short description of what it does
• A SYNOPSIS of its usage, including available switches
• A longer DESCRIPTION of the command’s functionality
• A switch-by-switch listing of its OPTIONS
• Any FILES associated with the command
• Any known BUGS in the command
• EXAMPLES, showing how to use the command
• A SEE ALSO section for further reference
All man pages on a system are collectively called the Linux Manual. The Linux Manual is also divided into sections, each of which covers a particular topic. Every man page is associated with one of these sections.
Wednesday, November 18, 2009
Lesson04:Executing Commands
Executing Commands
In this lesson, you will study how to run commands at the command prompt, and in the process, you will examine some simple commands.
After completing this lesson, you will be able to meet the following objectives:
• Run commands at the command line
• Use the date and cal commands
Running Commands
Commands have the following general syntax:
command options arguments
When you enter a command but do not get any prompt back, the command may be busy executing or may be waiting for input.To interrupt a command that is taking too long to execute, type Ctrl-C.
Occasionally you might enter a command without an argument, where the command waits for input to come from the keyboard. In this case, type Ctrl-C to terminate the command.
You can use semicolons to separate multiple commands on the same line. When the first command finishes, the next one will execute.
For example:
Simple Commands: Examples
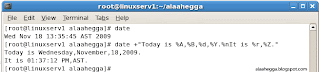
The date command prints the system date and time.To configure the format, you can use optional formatting strings. For more information, run the date --help command.
This example demonstrates configuring the format of the date command.
date
date +"Today is %A,%B,%d,%Y.%nIt is %r,%Z."
You can also set the system time using the date command. To do this, use the date --set command. For example, to set the system clock forward by 40 minutes, use the following:
date --set="+40 minutes"
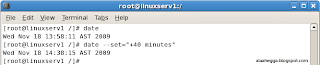
For more command options, con sult the man pages for the date command. Use the following:
man date
The cal command prints an ASCII calendar of the current month (by default, with no arguments provided). When provided with a single numeric argument, the cal command will give a calendar for the given year. Remember to use a four-digit year; the command cal 09 will give a calendar for the year 09, not the year 2009.
If cal is provided with a month and year as arguments, it will display the calendar for that particular month.
For example:
Saturday, November 14, 2009
RedHat Enterprise Linux Server Installation On VMWare
RedHat Enterprise Linux Server 5.2 Installation On VMWare 7.0
In this post I'll explain the installation of RedHat Enterprise Linux 5 on VMWare 7.0 ......
RedHat Enterprise Linux Server 5.2 Installation On VMWare 7.0 from alaahegga on Vimeo.
Tuesday, November 10, 2009
Sunday, November 8, 2009
Download Books :100 Success Secrets on RHCE Linux Test Preparation, Study Guides
Friday, November 6, 2009
Your way to take RHCE Study Materials and Tools For RHCE:::الطريق الى الحصول على شهادة الينكس RHCE
Tools
1-Two Redhat Enterprise Linux 5 Client latest 5.4 or Centos 5.4 client
2-one RedHat Enterprise Linux 5 Server lates 5.4 or Centos 5.4 Server
Download RHEL5.4 and Centos 5.4 torrnet
http://www.4shared.com/file/147268966/35a7c15f/Red_Hat_Enterprise_Linux_54_server_mininova.html
http://www.4shared.com/file/147269051/37835bd5/CentOS-54-i386-bin-DVD_mininova.html
or
Redhat Enterprise Linux V5.4 DVD
http://rapidshare.com/files/278306219/h-re548d.r00
http://rapidshare.com/files/278307216/h-re548d.r01
http://rapidshare.com/files/278304250/h-re548d.r02
http://rapidshare.com/files/278307318/h-re548d.r03
http://rapidshare.com/files/278305706/h-re548d.r04
http://rapidshare.com/files/278306566/h-re548d.r05
http://rapidshare.com/files/278304749/h-re548d.r06
http://rapidshare.com/files/278306818/h-re548d.r07
http://rapidshare.com/files/278303261/h-re548d.r08
http://rapidshare.com/files/278307378/h-re548d.r09
http://rapidshare.com/files/278307606/h-re548d.r10
http://rapidshare.com/files/278304810/h-re548d.r11
http://rapidshare.com/files/278306836/h-re548d.r12
http://rapidshare.com/files/278303696/h-re548d.r13
http://rapidshare.com/files/278306127/h-re548d.r14
http://rapidshare.com/files/278303702/h-re548d.r15
http://rapidshare.com/files/278305921/h-re548d.r16
http://rapidshare.com/files/278306111/h-re548d.r17
http://rapidshare.com/files/278303235/h-re548d.r18
http://rapidshare.com/files/278306614/h-re548d.r19
http://rapidshare.com/files/278304729/h-re548d.r20
http://rapidshare.com/files/278304211/h-re548d.r21
http://rapidshare.com/files/278306276/h-re548d.r22
http://rapidshare.com/files/278304457/h-re548d.r23
http://rapidshare.com/files/278304657/h-re548d.r24
http://rapidshare.com/files/278306514/h-re548d.r25
http://rapidshare.com/files/278304744/h-re548d.r26
http://rapidshare.com/files/278303824/h-re548d.r27
http://rapidshare.com/files/278306211/h-re548d.r28
http://rapidshare.com/files/278305541/h-re548d.r29
http://rapidshare.com/files/278305035/h-re548d.r30
http://rapidshare.com/files/278305789/h-re548d.r31
http://rapidshare.com/files/278304483/h-re548d.r32
http://rapidshare.com/files/278303690/h-re548d.r33
http://rapidshare.com/files/278306516/h-re548d.r34
http://rapidshare.com/files/278304776/h-re548d.r35
http://rapidshare.com/files/278307273/h-re548d.r36
http://rapidshare.com/files/278307729/h-re548d.r37
http://rapidshare.com/files/278305997/h-re548d.r38
http://rapidshare.com/files/278307187/h-re548d.r39
http://rapidshare.com/files/278306265/h-re548d.r40
http://rapidshare.com/files/278305186/h-re548d.r41
http://rapidshare.com/files/278307570/h-re548d.r42
http://rapidshare.com/files/278305877/h-re548d.r43
http://rapidshare.com/files/278307506/h-re548d.r44
http://rapidshare.com/files/278305083/h-re548d.r45
http://rapidshare.com/files/278307074/h-re548d.r46
http://rapidshare.com/files/278305282/h-re548d.r47
http://rapidshare.com/files/278306940/h-re548d.r48
http://rapidshare.com/files/278304833/h-re548d.r49
http://rapidshare.com/files/278304248/h-re548d.r50
http://rapidshare.com/files/278308004/h-re548d.r51
http://rapidshare.com/files/278305680/h-re548d.r52
http://rapidshare.com/files/278303207/h-re548d.r53
http://rapidshare.com/files/278307183/h-re548d.r54
http://rapidshare.com/files/278303800/h-re548d.r55
http://rapidshare.com/files/278305959/h-re548d.r56
http://rapidshare.com/files/278307773/h-re548d.rar
http://rapidshare.com/files/278305666/h-re548d.sfv
http://rapidshare.com/files/278303673/hotiso.nfo
Password:http://wareznet.net/
Or
CD1
http://hotfile.com/dl/8868035/0720e1e/RHE5-CD1.part1.rar.html
http://hotfile.com/dl/8868050/4accadc/RHE5-CD1.part2.rar.html
http://hotfile.com/dl/8868065/c5aa975/RHE5-CD1.part3.rar.html
http://hotfile.com/dl/8868082/ca153b6/RHE5-CD1.part4.rar.html
http://hotfile.com/dl/8868107/ebf6277/RHE5-CD1.part5.rar.html
http://hotfile.com/dl/8868122/8e54730/RHE5-CD1.part6.rar.html
http://hotfile.com/dl/8868145/1182f89/RHE5-CD1.part7.rar.html
CD2
http://hotfile.com/dl/8868165/2d67531/RHE5-CD2.part1.rar.html
http://hotfile.com/dl/8868179/48a0d22/RHE5-CD2.part2.rar.html
http://hotfile.com/dl/8868194/89ad13d/RHE5-CD2.part3.rar.html
http://hotfile.com/dl/8868217/f71a46c/RHE5-CD2.part4.rar.html
http://hotfile.com/dl/8868229/2503e8a/RHE5-CD2.part5.rar.html
http://hotfile.com/dl/8868248/d842206/RHE5-CD2.part6.rar.html
http://hotfile.com/dl/8868267/1986139/RHE5-CD2.part7.rar.html
http://hotfile.com/dl/8868274/04b8434/RHE5-CD2.part8.rar.html
CD3
http://hotfile.com/dl/8868290/14685db/RHE5-CD3.part1.rar.html
http://hotfile.com/dl/8868300/4b6a0d2/RHE5-CD3.part2.rar.html
http://hotfile.com/dl/8868321/9ac268b/RHE5-CD3.part3.rar.html
http://hotfile.com/dl/8868371/29f2df0/RHE5-CD3.part4.rar.html
http://hotfile.com/dl/8868390/f656303/RHE5-CD3.part5.rar.html
http://hotfile.com/dl/8868404/76d4d4e/RHE5-CD3.part6.rar.html
http://hotfile.com/dl/8868421/3d498bf/RHE5-CD3.part7.rar.html
http://hotfile.com/dl/8868426/b08e74a/RHE5-CD3.part8.rar.html
CD4
http://hotfile.com/dl/8868444/22fb1c6/RHE5-CD4.part1.rar.html
http://hotfile.com/dl/8868460/1fe1e93/RHE5-CD4.part2.rar.html
http://hotfile.com/dl/8868488/33bac14/RHE5-CD4.part3.rar.html
http://hotfile.com/dl/8868505/c28d3c0/RHE5-CD4.part4.rar.html
http://hotfile.com/dl/8868526/4bab411/RHE5-CD4.part5.rar.html
http://hotfile.com/dl/8868545/4f964bd/RHE5-CD4.part6.rar.html
http://hotfile.com/dl/8868558/ea17158/RHE5-CD4.part7.rar.html
http://hotfile.com/dl/8868567/d6b0c07/RHE5-CD4.part8.rar.html
CD5
http://hotfile.com/dl/8868582/defd4c3/RHE5-CD5.part1.rar.html
http://hotfile.com/dl/8868593/8d054d6/RHE5-CD5.part2.rar.html
http://hotfile.com/dl/8868595/2300b48/RHE5-CD5.part3.rar.html
Download Centos DVD
http://rapidshare.com/files/250286018/centos5.rar
http://rapidshare.com/files/149209427/CentOS-5.1-i386-bin-DVD.part01.rar
http://rapidshare.com/files/149221522/CentOS-5.1-i386-bin-DVD.part02.rar
http://rapidshare.com/files/149232257/CentOS-5.1-i386-bin-DVD.part03.rar
http://rapidshare.com/files/149242291/CentOS-5.1-i386-bin-DVD.part04.rar
http://rapidshare.com/files/149251798/CentOS-5.1-i386-bin-DVD.part05.rar
http://rapidshare.com/files/149261091/CentOS-5.1-i386-bin-DVD.part06.rar
http://rapidshare.com/files/149270602/CentOS-5.1-i386-bin-DVD.part07.rar
http://rapidshare.com/files/149279383/CentOS-5.1-i386-bin-DVD.part08.rar
http://rapidshare.com/files/149287578/CentOS-5.1-i386-bin-DVD.part09.rar
http://rapidshare.com/files/149295917/CentOS-5.1-i386-bin-DVD.part10.rar
http://rapidshare.com/files/149304578/CentOS-5.1-i386-bin-DVD.part11.rar
http://rapidshare.com/files/149318688/CentOS-5.1-i386-bin-DVD.part12.rar
http://rapidshare.com/files/149329692/CentOS-5.1-i386-bin-DVD.part13.rar
http://rapidshare.com/files/149341526/CentOS-5.1-i386-bin-DVD.part14.rar
http://rapidshare.com/files/149368468/CentOS-5.1-i386-bin-DVD.part15.rar
http://rapidshare.com/files/149385589/CentOS-5.1-i386-bin-DVD.part16.rar
http://rapidshare.com/files/149401389/CentOS-5.1-i386-bin-DVD.part17.rar
http://rapidshare.com/files/149416961/CentOS-5.1-i386-bin-DVD.part18.rar
http://rapidshare.com/files/149432530/CentOS-5.1-i386-bin-DVD.part19.rar
http://rapidshare.com/files/149447991/CentOS-5.1-i386-bin-DVD.part20.rar
http://rapidshare.com/files/149465432/CentOS-5.1-i386-bin-DVD.part21.rar
http://rapidshare.com/files/149481458/CentOS-5.1-i386-bin-DVD.part22.rar
http://rapidshare.com/files/149495840/CentOS-5.1-i386-bin-DVD.part23.rar
http://rapidshare.com/files/149509612/CentOS-5.1-i386-bin-DVD.part24.rar
http://rapidshare.com/files/149521508/CentOS-5.1-i386-bin-DVD.part25.rar
http://rapidshare.com/files/149532200/CentOS-5.1-i386-bin-DVD.part26.rar
http://rapidshare.com/files/149542113/CentOS-5.1-i386-bin-DVD.part27.rar
http://rapidshare.com/files/149551165/CentOS-5.1-i386-bin-DVD.part28.rar
http://rapidshare.com/files/149560270/CentOS-5.1-i386-bin-DVD.part29.rar
http://rapidshare.com/files/149569313/CentOS-5.1-i386-bin-DVD.part30.rar
http://rapidshare.com/files/149577389/CentOS-5.1-i386-bin-DVD.part31.rar
http://rapidshare.com/files/149586578/CentOS-5.1-i386-bin-DVD.part32.rar
http://rapidshare.com/files/149595742/CentOS-5.1-i386-bin-DVD.part33.rar
3- VMWare Workstation latest 7.0 or Sun VirtualBOX 3.0.8
Windows
http://hotfile.com/dl/16010851/31e9c9e/VmW700203739WiN.part1.rar.html
http://hotfile.com/dl/16010848/2f0a098/VmW700203739WiN.part2.rar.html
Linux
http://hotfile.com/dl/15948303/cf1fb0e/VmW700203739NuX.rar.html
http://uploading.com/files/e588a6f9/VirtualBox-3.0.8-53138-Win.rar
Books and Materials
1-RHCE Red Hat Certified Engineer Linux Study Guide (Exam RH302), Fifth Edition by Michael Jang.
Password:alaahegga.blogspot.com
2-Red Hat Ent. Linux Deployment Guide
3-Red Hat Enterprise Linux Install Guide
4-Red Hat Virtualization
5-Cluster Suite for Red Hat Ent. Linux 5
6-Configuring/Managing a Red Hat Cluster
7-Configuring/Managing a Red Hat Cluster
8-Red Hat Magazine
9-Red Hat Videos
10-News Blog
CBT
Downloads
1-LinuxCBT Enterprise Linux 5 Edition EL-5- RS
http://rapidshare.com/files/218057105/LinuxCBT_-_RHEL5.part01.rar.html
http://rapidshare.com/files/218057116/LinuxCBT_-_RHEL5.part02.rar.html
http://rapidshare.com/files/218057103/LinuxCBT_-_RHEL5.part03.rar.html
http://rapidshare.com/files/218057104/LinuxCBT_-_RHEL5.part04.rar.html
http://rapidshare.com/files/218073841/LinuxCBT_-_RHEL5.part05.rar.html
http://rapidshare.com/files/218124489/LinuxCBT_-_RHEL5.part06.rar.html
http://rapidshare.com/files/218124559/LinuxCBT_-_RHEL5.part07.rar.html
http://rapidshare.com/files/218124662/LinuxCBT_-_RHEL5.part08.rar.html
http://rapidshare.com/files/218125844/LinuxCBT_-_RHEL5.part09.rar.html
http://rapidshare.com/files/218156280/LinuxCBT_-_RHEL5.part10.rar.html
http://rapidshare.com/files/218226789/LinuxCBT_-_RHEL5.part11.rar.html
http://rapidshare.com/files/218229434/LinuxCBT_-_RHEL5.part13.rar.html
http://rapidshare.com/files/218228179/LinuxCBT_-_RHEL5.part12.rar.html
http://rapidshare.com/files/218259169/LinuxCBT_-_RHEL5.part15.rar.html
http://rapidshare.com/files/218258229/LinuxCBT_-_RHEL5.part14.rar.html
http://rapidshare.com/files/218303700/LinuxCBT_-_RHEL5.part16.rar.html
http://rapidshare.com/files/218304752/LinuxCBT_-_RHEL5.part18.rar.html
http://rapidshare.com/files/218304462/LinuxCBT_-_RHEL5.part17.rar.html
http://rapidshare.com/files/218338769/LinuxCBT_-_RHEL5.part22.rar.html
http://rapidshare.com/files/218338243/LinuxCBT_-_RHEL5.part21.rar.html
http://rapidshare.com/files/218314969/LinuxCBT_-_RHEL5.part20.rar.html
http://rapidshare.com/files/218314540/LinuxCBT_-_RHEL5.part19.rar.html
http://rapidshare.com/files/218347640/LinuxCBT_-_RHEL5.part24.rar.html
http://rapidshare.com/files/218338857/LinuxCBT_-_RHEL5.part23.rar.html
http://rapidshare.com/files/218228073/LinuxCBT_-_RHEL5.part25.rar.html
http://rapidshare.com/files/218057090/LinuxCBT_-_RHEL5.part25.rar.html
2-VTC Red Hat Certified Engineer RHCE Tutorials
Part 01 : http://bit.ly/2Rqi4Z
Part02 : http://bit.ly/20A0Qf
Part03 : http://bit.ly/48GWWk
password:~kiddu~
Monday, November 2, 2009
All Last Three Lessons :: جميع الدروس السابقه
All Last Three Lessons :: جميع الدروس السابقه
Lesson01 Part01
Lesson01 Part02
Lesson02 Part01
Lesson02 Part02
Lesson03 Part01
Lesson03 Part02
Lesson03 Part03
Sunday, November 1, 2009
VTC Red Hat Certified Engineer RHCE Tutorials
VTC Red Hat Certified Engineer RHCE Tutorials :: شرح دورة RHCE 
Introduction
Welcome (05:28) T
System Requirements (02:54) T
Additional Information for the RHCE Exam
What Else to prepare for the RHCE Exam (02:09) T
Logical Volume Management (04:07) T
Logical Volumes During Installation (06:00) T
Logical Volumes After Installation Pt.1 (02:20) T
Logical Volumes After Installation Pt.2 (06:09) T
Setting up a Kickstart File (04:49) T
An Automated Kickstart Installation (03:48) T
Reviewing Rescue Mode (06:23) T
Problems during the boot process (04:35) T
What can go wrong with GRUB (07:36) T
Create a network installation server (05:01) T
System Monitoring and Fault Analysis
System Performance and Security Concepts (04:46) T
System Faults and Breaches (05:00) T
Method of Fault Analysis (03:03) T
Benefits of System Monitoring (03:20) T
Managing Process by Account (02:24) T
System Service Analysis
System Service Access Controls (06:48)
Service and Network Access Controls (04:30)
Service and Application Access Controls (03:06)
tcp_wrappers Configuration (04:11)
Security Enhanced Linux (SELinux) (05:09)
Network Configuration and Security
Network Resource Access Controls (03:20)
Dynamic Interface Configuration (03:48)
Static Interface Configuration (03:10)
Routing Configuration Pt.1 (02:28)
Routing Configuration Pt.2 (05:52)
Netfilter Overview (06:11)
iptables Firewall Rules (06:09)
Firewall Rules by IP address (06:21)
Network Access Translation (NAT) (03:17)
Network Support Services
Organizing Networked Systems (02:08)
Host Name Resolution (03:07)
Trace a DNS Query with the dig command (02:47)
Exploring DNS with the host command (02:49)
An Overview of Domain Name Services (03:15)
DNS Packages (05:14)
Configuring a BIND Caching Nameserver (06:40)
Setting up a Slave Nameserver (05:17)
BIND in sysconfig and command support (04:04)
The DHCP Service (05:57)
Configuring an NTP Server (05:37)
Sharing on a Network
Network File Sharing Services (02:26)
FTP – Basic Server Configuration (05:05)
FTP – Security Options (06:09)
NFS – Basic Server Configuration (03:47)
NFS – Security Options (04:49)
Samba – Basic Server Configuration (06:10)
More on Samba (06:25)
Samba Security Options (03:59)
File Server Security (03:28)
Apache Web Services and More
Apache Web Services (03:02)
Critical Apache Configuration Directives (06:28)
Creating a Virtual Host (06:55)
Limiting Access to an Apache Website (05:33)
Apache and SELinux (03:39)
Creating a Secure Apache Host (07:24)
Configuring the Squid Web Proxy (05:27)
Configuring Email Services
Email Protocols and Agents (04:02)
Basic sendmail Configuration Pt.1 (04:33)
Basic sendmail Configuration Pt.2 (03:38)
Basic Postfix Configuration (04:33)
Switching Between SMTP Services (02:47)
Mail Retrieval Protocols (03:39)
Creating Secure Remote Access
A Secure Shell Server (06:17)
Configuring Secure Certificates (05:24)
Secure Shell Keys (07:10)
Account Security
Basic Account Management (03:02)
Name Service Switching (04:19)
Pluggable Authentication Modules (PAM) (04:19)
Utilities and Authentication (04:52)
Making PAM Work For You (05:57)
Troubleshooting and System Maintenance
Use the Rescue Environment (06:38)
Diagnose and Correct Boot Failures (06:04)
Address Problems with Network Services (06:04)
Add, Remove, and Resize Logical Volumes (03:22)
Diagnose SELinux Network Problems (02:32)
Installation and Configuration
Install Packages for Network Services (04:08)
Configure SELinux for Network Services (02:49)
Configure Services to Start on Boot (03:43)
Configure Basic Service Operation (03:29)
Configure User/Host-based Security (03:52)
Configure Kickstart Installations (02:45)
Add Logical Volumes during Installation (03:47)
Use iptables to for Firewalls and NAT (04:33)
Use PAM for User-Level Restrictions (03:35)
Wrap-up Wrap-up Pt.1 (03:33)
Wrap-up Pt.2 (05:36)
Credits
About the Author (01:23)
Downloads
Part 01 : http://bit.ly/2Rqi4Z
Part02 : http://bit.ly/20A0Qf
Part03 : http://bit.ly/48GWWk
password:~kiddu~
Friday, October 30, 2009
Thursday, October 29, 2009
Lesson03(Part03):Linux Basics Continued
Lesson03:Linux Basics Continued
Creating Passwords
The combination of login name and password controls access to the system. To maintain the security level of the system, passwords need to be both hard to guess and changed regularly.
The rules for creating strong passwords are fairly well understood, and are as follows:
1. Use a minimum of eight characters; more characters are better, as long as you are comfortable remembering and typing them
2. Do not base the password on a dictionary word
3. Use a variety of different types of characters; use at least three of the following:
a. Lowercase letters
b. Uppercase letters (Linux passwords are case sensitive)
c. Numbers
d. Punctuation marks and other special characters
4. Avoid using your real name, login name, or variations thereof; for example, with a login name of sally, a poor password would be s@lly
5. Avoid using easy-to-determine personal information, such as your birthday, anniversary, etc.
6. Avoid using formulas, such as 1+1=2
7. Avoid excessive complexity if it tempts you to perform such unsafe practices as writing the password onto a notepad near your monitor
Changing Passwords
Passwords can be changed from the terminal or the GUI. Through GNOME, navigate to System > Preferences > About Me, and then click Change Password. From the terminal, use the passwd command.
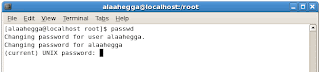
Before the system will allow you to change your password, it will require you to supply your current password. You will then be required to enter your new password twice to ensure that you did not make a typing mistake. Characters entered when typing a password are never echoed back to the screen.
The system, by default, performs some checks to ensure that a weak password has not been chosen. If you enter a weak password, the system will return an error message and allow you to try again.
The root User
The administrative account, also called the superuser account, is called root. The root user has an almost unlimited capability to manipulate the system, and can do the following:
• Read, modify, or delete any file
• Change into any directory
• Modify system configuration files
• Perform almost any other task on the system
That being said, this also implies you can do virtually unlimited damage to the system, corrupting or deleting all files, either by design or accident. A normal user’s potential to do damage is more limited.
For this reason, it is essential that you do not log in as the root user unless absolutely necessary. Also remember to log out of the root account as soon as possible.
Changing Identities
To change identities, use the su command.
The syntax for the su command is as follows:
su [option] [-] [username [arguments] ]
If no username is provided, su assumes that you want to switch to the root user. If a username is provided (for example, su - joe), the resulting shell will run as that user instead. su always prompts for the user’s password unless you are running it as root. root may access any account without providing a password.
When a hyphen (-) is passed as an argument to su (for example, su -), a login shell is created. Otherwise a non-login shell is created. The distinction between these types of shells will be discussed in detail later. For now, suffice it to say that, especially when becoming root, certain important settings are inherited by login shells, but not by non-login shells. So it is considered best practice to always use the - option when running su.
To elevate your privileges just for the run time of one command, use the sudo command.
You can also use sudo followed by a command to elevate your privileges just for the run time of this command. For example, sudo passwd joe, would run passwd with root privileges, allowing a non-root user to change joe’s password. To use sudo, a system administrator needs to have granted you access ahead of time; the system administrator can control which commands you may run with elevated privileges. Only users listed in the /etc/sudoers configuration file are allowed to use the sudo command. To edit the /etc/sudoers configuration file, as root, run the visudo command. Details of configuring sudo are outside the scope of this course, though some basic configuration will be covered later.
Usually, sudo prompts you for a password. The password being requested is your password, not root’s. This is to prevent someone else sneaking up to your terminal and abusing your sudo privileges.
With all these options for changing your identity, it becomes very useful to be able to check who you are and what groups you are in. You can do this with the id command. This command, as shipped with RHEL 5, is SELinux-aware and can also display the default SELinux context of processes you run when given the -Z switch. You can also view information on other users by running ID username.
Editing Text Files
As you already know, a central feature of Linux is that configuration files typically are plain text files. Plain text is also a common format on Linux, so it is vital that users be familiar with a plain text editor.
Various plain text editors are available in Red Hat Enterprise Linux. The most popular, powerful, and widely used plain text editor in the Linux and UNIX world is vi—its upgraded version is vim. Since many of the features that make vim so powerful also make it difficult for beginners to use, it is helpful for users to know a simple editor before beginning the adventure that is vim.
One of the easiest editors to learn is nano, a plain text editor that runs in a terminal window. It is available on most all Red Hat Enterprise Linux systems. To start nano, simply type the nano command. You may specify a file on the command line by giving the file name as an argument. If the file exists, you will edit it; if it does not exist, nano will create the file when you save it.
Once in nano, you simply type the text you wish to add; use the arrow keys to move the cursor around the file or use the Delete or Backspace keys to forward delete or backspace over text.file when you save it.
Other commands in nano are run using the Ctrl key. The last two lines on the screen display a menu of commands to run. Typically, the menu will look like the one shown here.
The caret (^) in the menu stands for Ctrl. For example, ^X means that you can type Ctrl-X to exit.
Wednesday, October 28, 2009
تغير طريقة واسلوب امتحان الريد هات RHCEng ::RHCE exam method and style was changed
تغير طريقة واسلوب امتحان الريد هات RHCEng ::RHCE exam method and style was changed
Launch of RHCEng (next generation RHCT & RHCE Examination)
Item Presentation (Electronic)
Structure of examination and duration
The mode of the exam remains the same i.e., Performance Based Testing.
Major changes
Hardware Requirements
Download pdf
Lesson03(Part02):Linux Basics Continued
Lesson03:Linux Basics Continued
Logging In to a Linux System continued
A typical Linux system will run six virtual consoles and one graphical console, but there are exceptions: a server system often only has virtual consoles, whereas a desktop and workstation typically have both.
Elements of the X Window System
A desktop environment is a collection of configurations and tools that define how a graphical environment should look. Red Hat provides these desktop environments:
2. KDE: An alternate desktop environment
Starting the X Server
2. Run the startx command
Tuesday, October 27, 2009
Download Books : RHCE by Michael Jang
RHCE Red Hat Certified Engineer Linux Study Guide (Exam RH302), Fifth Edition by Michael Jang.
This book contains hundreds of practice questions and hands-on exercises, this authoritative guide covers what you need to know--and shows you how to prepare for the challenging RHCE exam (RH302).
Download Now RHCE 302
Password:alaahegga.blogspot.com
Monday, October 26, 2009
lesson03(Part01): Linux Basics
Logging In to a Linux System
To gain access to a system, you are required to go through the authentication process, which is most commonly used to authenticate a user. To gain authentication, you must enter a valid user name and password at the login prompt.
When logging in at the system console, you are presented with either a text-based or graphical login (display manager).
If you are in run level 3 as in the below image:
If you are in run level 5 as in the below image:
After logging process, you will be access the Linux command line(runlevel 3 #init 3) as depicts in the below image :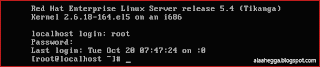
and the below image in GUI mode X11 run level ( runlevel 5 #init 5)
Lesson03 : Linux Basics Continued
Thursday, October 22, 2009
Lesson02:Linux Distributions and Linux Essentials Continued
- Everything in Linux is represented by a file (including hardware)
- Small, single-purpose programs are used
- The capability to chain programs together enables performing complex tasks
- Using captive user interfaces is avoided
- Configuration data is stored in text
UNIX systems have numerous utilities designed to create and manipulate files. The UNIX security model is based on the security of files. By treating everything as a file, consistency can be maintained. This allows you to secure access to hardware in the same way as you would secure access to a document.
UNIX provides many small utilities that perform one task very well. The general idea is to create a separate program when you require new functionality rather than extend an existing utility with new features.
A core design feature of UNIX is that the output of one program can serve as the input for another. This provides the user with the capability to chain many small programs together to perform a larger, more complex task.
Interactive commands are uncommon in UNIX. For most commands, the user needs to type their options and arguments on the command line
when the command is launched. The command completes normally, possibly producing output or it generates an error message and quits.
Interactivity is reserved for programs where it serves best, for example, with text editors (of course, some text editors are not
interactive).
Text is a universal interface, and many UNIX utilities exist to manipulate text. Storing configuration data in text allows the
administrator to easily move a configuration from one system to another.
Lesson02:Linux Distributions and Linux Essentials
Red Hat Distributions
Linux distributions are operating systems based on the Linux kernel.
Two important Red Hat distributions are Red Hat Enterprise Linux and the Fedora Project, described below.
Red Hat Enterprise Linux comprises very thoroughly tested software and is stable. It has professional support services and centralized management tools for large networks.

The Fedora Project comprises newer, bleeding-edge applications and technologies. It is supported by the community and has no formal Red Hat support. Fedora is mainly targeted to personal systems.
The Fedora Project is a collection of community-supported open source projects that is sponsored by Red Hat. Its purpose is to encourage rapid progress of free and open source software. The product is called Fedora and it is designed to be an incubator and test bed for new technologies that may be used in later Red Hat Enterprise products.
Wednesday, October 21, 2009
Linux Training Companies In Egypt::::شركات تدريب اللينكس فى مصر
Master Linux :: ماستر لينكس
Address: 48, Abass El-Akad St,Nasr City, Cairo – Egypt In front of ElBatrawy Street .
Phone : +2 02 22 65 444 6
Mobile : +2 017 345 1515
+2 010 44 55 935
Linux Plus:: لينكس بلس
Address:Saray El-Maadi Office Building Tower (A)- 1st Floor,35A Cornich El-Nil Street,
(next to Nile Badrawy Hospital)Maadi, Cairo, Egypt.
Tel. :+202 25 27 66 16
Tel. :+202 25 24 07 45
Fax. :+202 25 26 10 55
Mobile:+2012 78 4 666 5
E-mail: info@linux-plus.com
Information Technology Institute::معهد تكنولوجيا المعلومات
Cairo Branch
Address: 241 El-Aharam St.,Giza
Tel: +202-33868420
+202-33862131
Fax: +202-33868429
Email: info@iti.net.eg
Alexandria Branch
Address: 1 Mahmoud Said St., Shohada Square, Main Post Office Building, Alexandria.
Tel: +203-3906924
+203-3906925
+203-3906926
Fax: +203-3906924
Mansoura Branch
Address: Mansoura University, Amal City for Male (University Hostel for Male).
Tel: +2050-2364279
Fax: +2050-2361659
Assiut Branch
Address: Assuit University, Network Information Building,Assuit.
Tel: +2088-2374264
+2088-2374265
Fax: +2088-2374264
Hotline
19YAT
19928
Headquarter
6th Floor 68, Makram Ebaid St., Nasr City,
Cairo - Egypt
Tel: 2 02 22750842
Fax: 2 02 22749356
Email: info@yat.com.eg
Heliopolis Branch
15, M. Yousief El Kady St., Kolleyet El Banat, Heliopolis,
Cairo - Egypt
Tel: 2 02 24175036
Fax: 2 02 24144738
Email: heliopolis@yat.com.eg
Nasr City Branch
5th Floor 68, Makram Ebaid St., Nasr City,
Cairo – Egypt
Tel: 2 02 22750842
Fax: 2 02 22749356
Email: nasrcity@yat.com.eg
Maadi Branch
48, Street No. 7, Maadi,
Cairo - Egypt
Tel: 2 02 23584433
Fax: 2 02 23580547
Email:maadi@yat.com.eg
Mohandeseen Branch
8, El Batal Ahmed Abdel Aziz St., Mohandeseen,
Giza- Egypt
Tel: 2 02 33360225
Fax: 2 02 33360363
Email: mohandessen@yat.com.eg
Dokki Branch
El Mesaha Square, Dokki,
Cairo – Egypt
Tel: 2 02 337628773
Fax: 2 02 337628774
Email: Dokki@yat.com.eg
Alexandria Branch
28 Essam Helmy St., Smouha,
Alexandria - Egypt
Tel: 2 03 4271378
Fax: 2 03 4271378
Email: smouha@yat.com.eg
Tanta Branch
9 Moaweya St., Tanta
Elgharbia - Egypt
Tel: 040 3299035
Fax: 040 3299036
Email :tanta@yat.com.eg
Mansoura Branch
95 El-Gomhoreya St., Mansoura
Eldakahlia - Egypt
Tel: 050 2223064
Fax: 050 2223065
E-mail: mansoura@yat.com.eg
Port Said Branch
6 Elseid Port-The intersection of El-Gomhoreya St with Delecips
Port Said - Egypt
Tel:066 3245202
Fax: 066 3244503
Email: portsaid@yat.com.eg
Assiut Branch
74 Makka El-Mokarama St. of Gomhorya St,
Assiut - Egypt
Tel: 2 088 295633
Fax: 2 088 295622
Email: assiut@yat.com.eg
New Horizons Alexandria, Egypt
431 El Horreya Rd.
Roushdy
Alexandria, ALY, 21311 Egypt
Phone :+ 203-543-0820
sales.alexandria@newhorizons.com
New Horizons Cairo, Egypt
6 October Magda Center,
7th Area, Central Axis
Cairo, , Egypt
Phone :002 02 837 1836
cairo.sales@newhorizons.com
Egypt (Dokki) New Horizons Cairo, Egypt (Dokki)
7 El Sad El Aaly St.
Vinni Square
Cairo, Giza, 12311 Egypt
Phone :+202-3-761-7013
cairo.sales@newhorizons.com
Egypt (Nasr City) New Horizons Cairo, Egypt (Nasr City)
8 Mohamed Mostafa Hamam ST.
Behind Pizza Hut Abbass El Akkad
Cairo, Egypt
Phone :+002 02 4024902
New Horizons Mansoura, Egypt
El Gomhoreya St
University Commercial center, Sun Mall
Mansoura, Dakahlia, ., . Egypt
Phone :+20-50-2239667
Tuesday, October 20, 2009
Monday, October 19, 2009
Others Linux Blogs
Others Linux blogs
http://linuxhelp.blogspot.com/
http://linuxoniphone.blogspot.com/
http://linuxondesktop.blogspot.com/
http://linux-society.blogspot.com/
http://tolearnfree.blogspot.com/
http://helpforlinux.blogspot.com/
http://info4linux.blogspot.com/
http://thelinuxmovement.blogspot.com/
http://linux-trial.blogspot.com/
http://adminlinux.blogspot.com/
http://vntutor.blogspot.com
http://unix-tutorial.blogspot.com/
http://neworacledba.blogspot.com/
http://jons-thoughts.blogspot.com/
http://linuxinterviews.blogspot.com/
http://idolinux.blogspot.com
http://unixnotebook.blogspot.com
http://almaaey.blogspot.com/
http://redhatcat.blogspot.com/
http://ccnacertificate.blogspot.com
http://gauravpartap.blogspot.com
Lesson 01 : Linux History continued
Open source software:
- The software and source code must be freely distributable
- All users must be able to modify the source code and create derived works
- To maintain the integrity of the original author’s work, the license may require that modifications to the code be provided in patch form
- The license has to be inherited, so that those who receive a distribution are subject to the identical terms
- The license must be nondiscriminatory with respect to persons, groups, or fields of endeavor; it must be free of restrictions that can limit the license. For example, it may not require that the software be a part of a particular distribution; it must not restrict other non-OSS software and it may not require the use of technology to apply the license.
An alternative definition of open source software comes from the free software movement, which emphasizes the ethical aspects of software and source code availability. As presented by the GNU Project and the Free Software Foundation at http://www.gnu.org/philosophy/free-sw.html, software is free if it satisfies four freedoms:
- The software must be freely executable for any purpose
- The source code must be available so that others can study how it works
- The software must be freely redistributable
- All users must be free to modify the software
Lesson 01 : Linux History

Newsgroups: comp.os.minix
Subject: What would you like to see most in minix?
Summary: small poll for my new operating system
Message-ID:1991AUG25.205708.9541@klaava.Helsinki.FI
Date: 25 Aug 91 20:57:08 GMT
Organization: University of Helsinki
Hello everybody out there using minix -
professional like gnu) for 386(486) AT clones. This has been brewing
since april, and is starting to get ready. I'd like any feedback on
things people like/dislike in minix, as my OS resembles it somewhat
(same physical layout of the file-system (due to practical reasons)
among other things).
This implies that I'll get something practical within a few months, and
I'd like to know what features most people would want. Any suggestions
are welcome, but I won't promise I'll implement them :-)
It is NOT protable (uses 386 task switching etc), and it probably never
will support anything other than AT-harddisks, as that's all I have :-(.
Free RHCE Training sample
Register free RHCE & RHCT levels elearning training demo sample.
http://bit.ly/2KEMg7
RHCE Training
In this topic I'll give some training materials for the Red Hat Certified Engineer Certificates
#Red Hat Authorized training
https://www.redhat.com/courses/
https://www.redhat.com/elearning/
http://virtualclass.cgselearning.com/cms/demo/redhat/demo_app.jsp